Asset inventory with Rumble on FreeBSD
Introduction
Inventory and control of your IT hardware and software based assets is one of the basic processes you must have in place managing and securing an IT infrastructure properly. At the same time it is probably one of the most difficult processes to implement. But this has changed now! No more scripts scanning your networks, using i.e. nmap.
Rumble is a network asset discovery tool and as of 2 June 2020 it is also available on FreeBSD!
On 24 April Rumble announced the introduction of the Starter Edition available as a free tier! And not long after that Rumble announced the availability of a native FreeeBSD based agent and scanner.
Below you can read how to implement and use Rumble on FreeBSD.
Rumble: an introduction
Rumble is a network asset discovery tool, created by H.D. Moore, who also created the Metasploit Framework. It helps security, network and system administrator engineers to identify connected servers, workstations, network equipment, such as routers, and other devices (like tablets, phones and IoT devices) within a network. It extracts all relevant properties possible from the found assets and collects the data. It then compares it to a very large fingerprint database, and show you its findings in a nice elegant and readable way. It also provides means to analyze the data.
Rumble uses a single or multiple agents running in your environment, which sends its data to the central Rumble GUI console.
You can also scan and keep the results locally using the Rumble Scanner.
Before you can start using Rumble, you have to register yourself. You can do so for the Starter Edition using this link. The paid options offer more functionality but for home environments the Starter Edition is more than sufficient!
Required for your scanner
You need curl to be able to install the Rumble Agent and Scanner. So use the below step to install the curl package on your FreeBSD host :
$ sudo pkg install curl
Implement the Rumble Agent
The steps to install the Rumble Agent are well documented and also stated in the Rumble GUI console once logged in (click ‘Agents’ in the left menu and then choose the ‘BSD Variants’ icon). The Rumble Agent you download and install is specifically for your Rumble account.
The following commands install the Rumble Agent on your FreeBSD server:
$ cd /usr/local/sbin $ sudo curl -o rumble-agent.bin \ https://console.rumble.run/download/agent/download token/account specific string/ \ rumble-agent-freebsd-amd64.bin $ sudo chmod 0555 /usr/local/sbin/rumble-agent.bin
The download link of the Rumble Agent is keyed to your Rumble organization using a donwload token and uses also a second account specific string. The download token is can be reset in the organization sessting page (click ‘Organizations’ under the Global Settings menu on the left and then click your arganization).
When installed the Rumble Agent can be started:
$ sudo /usr/local/sbin/rumble-agent.bin &
At this point in time Rumble does not supply a service script with the Agent. This will probably change in the near future. But luckely someone wrote one and shared it, you can find it here!
How to use the Rumble Agent
You use the Rumble Agent to perform scans on your network(s) which are initiated from the Rumble GUI console. You can configure a one time manual scan, but you can also schedule a scan with a certain frequency (i.e. daily, weekly, monthly).
Rumble uses the concept of sites. A sites is a collection of IP address(es) and or ranges. You can assign one site to the configuration of a network scan. Sites can be configured through the ‘Sites’ link in the left menu under ‘Organization Data’.
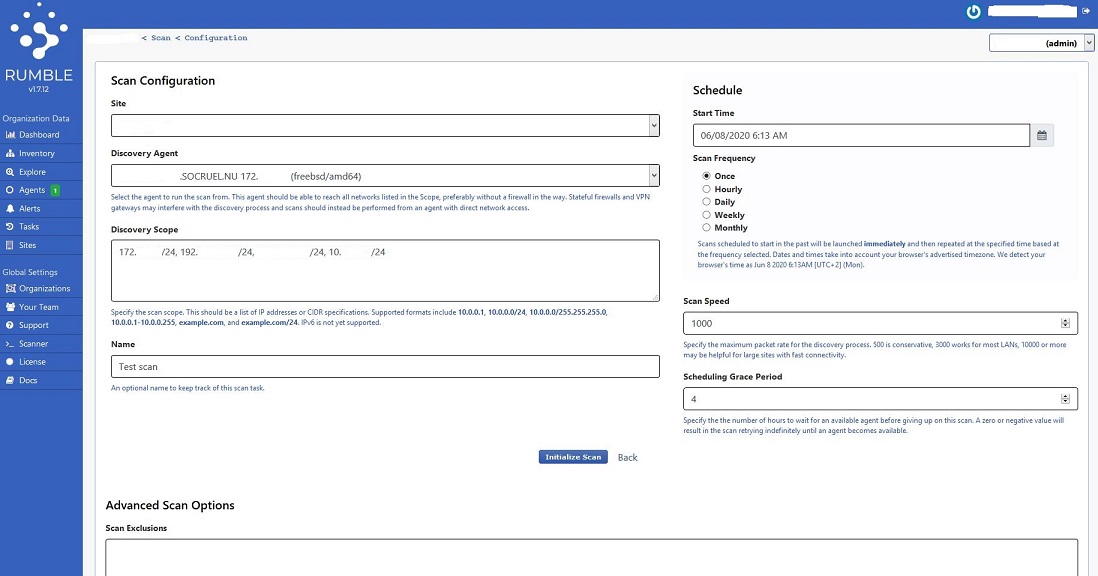
Implement the Rumble Scanner
Rumble provides also a Scanner which you, once installed, can use to perform network scans locally. The Scanner stores the results of a scan on the host where the Scanner is installed. You can upload a scan result to the Rumble GUI console if required.
The steps to install the Rumble Scanner are well documented and also stated in the Rumble GUI console once logged in (click ‘Agents’ in the left menu and then choose the ‘BSD Variants’ icon). The Rumble Scanner you download and install is specifically for your Rumble account.
The following commands install the Rumble Scanner on your FreeBSD server:
$ cd /usr/local/bin $ sudo curl -o rumble \ https://console.rumble.run/download/scanner/download token/account specific string/ \ rumble-scanner-freebsd-amd64.bin $ sudo chmod 0555 /usr/local/bin/rumble
How to use the Rumble scanner
The Rumble Scanner binary has a lot of options. To show all the options use the command:
$ rumble help
So you can i.e. scan a single IP with a specific range of TCP ports:
$ sudo rumble --tcp-ports 1-1024 10.101.102.3
Or you can scan a whole subnet with the default TCP port list:
$ sudo rumble 10.101.102.0/24
In both these examples the output is stored in a directory in the home directory of the user. the directory is created by the rumble binary.
You can specify where you want to store the output of your scan by using the -o option:
$ sudo rumble -o /var/tmp/inventory 10.101.102.0/24
The output of a scan with the rumble binary looks like the below:
user@scanner:rumble-20200605T132319 $ ll total 112K drwx------ 3 user user 512 Jun 5 13:23 . drwxr-xr-x 4 user user 512 Jun 5 13:24 .. -rw-r--r-- 1 user user 26 Jun 5 13:24 addresses_all.txt -rw-r--r-- 1 user user 26 Jun 5 13:23 addresses.txt -rw-r--r-- 1 user user 1515 Jun 5 13:23 assets.csv -rw-r--r-- 1 user user 21999 Jun 5 13:23 assets.html -rw-r--r-- 1 user user 6205 Jun 5 13:23 assets.jsonl -rw-r--r-- 1 user user 7327 Jun 5 13:23 bridges.html -rw-r--r-- 1 user user 48 Jun 5 13:23 hostnames.txt -rw-r--r-- 1 user user 8108 Jun 5 13:23 nmap.xml -rw-r--r-- 1 user user 220 Jun 5 13:23 protocols.csv -rw-r--r-- 1 user user 548 Jun 5 13:24 scan.log -rw-r--r-- 1 user user 15146 Jun 5 13:23 scan.rumble drwxr-xr-x 2 user user 512 Jun 5 13:23 screenshots -rw-r--r-- 1 user user 8255 Jun 5 13:23 topology.html
The output contains all obtained data in TXT, JSON, HTML and CSV formats. I want to look into the JSON format and see if I can make my own reports by extracting data using jq.
My observations so far
I’ve used Rumble for a couple of days when I write this post. So here some experiences and observations so far:
- first: the service of Rumble is absolutely great! My first scans using the FreeBSD scanner did not provide the detail of scans using an Ubuntu VM. So I highlighted this to the Rumble support team. Within a day (!) they identified the problem and issued a new version of the Rumble software, which solved the problem!
- Rumble scans much faster than i.e. nmap.
- the Rumble GUI console is intuitive and easy to use.
- the local Rumble Scanner is really a great addition to the Rumble Agent. This provides a lot of flexibility.
- it is important to have your DNS setup right and preferably have a PTR and A record configured for all of your assets.
- the SoCruel.NU platform runs a pfSense firewall, and Rumble did not recognise it as such. Probably because of the hardware I use (Protectli).
- my SNMP based Cisco switches are recognised, but not the OS of it.
- my non SNMP based Cisco switches are not recognised.
- I would like to see a mobile app to become available in the near future, such that I can see my assets on my mobile phone and/or tablet as well.
Conclusion
FreeBSD users have a great new network discovery tool to their disposal! I say, go out and implement it in your FreeBSD environment! You will not regret it!
Resources
Some (other) resources about this subject: